MVC APPLICATIONS AGAINST ATTACKERS
Introduction
Lot of ASP.NET MVC developers are great in delivery , writing high performance code and so on. But when it comes to security there is no planning done. So here we will run through 10 points which will help us to make our MVC code secure.
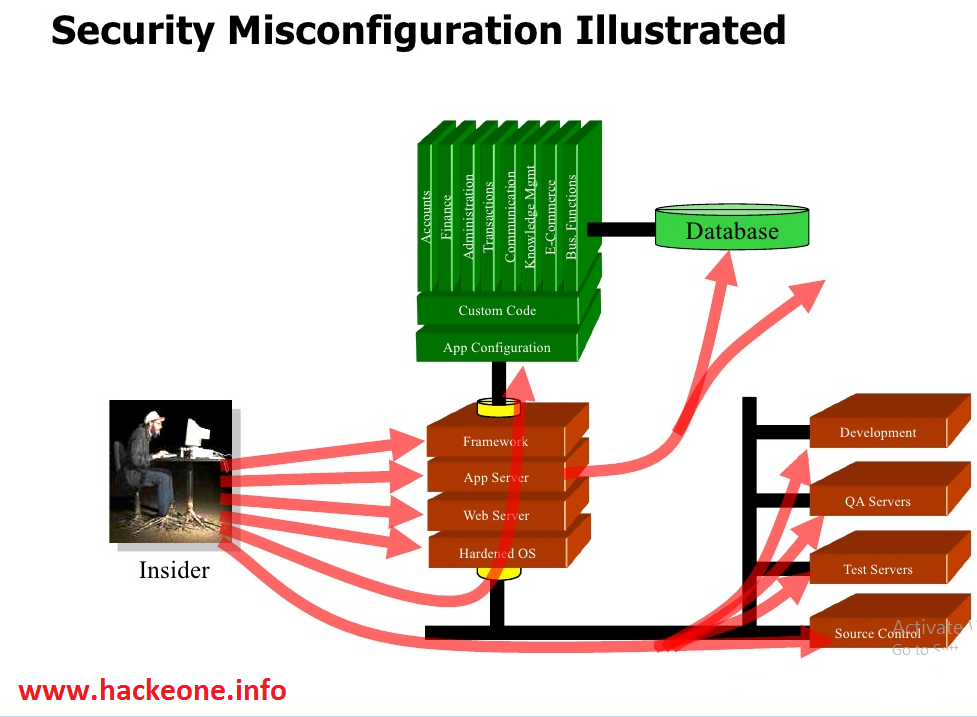
1- Security Misconfiguration:
In this kind of attack the attacker intercepts form data which is submitted by end User and changes values and sends the modified data to the server.
SOLUTION:
- Create a custom Error handling Attribute.
- Setting Custom Error page from Web.config file.
Emerging Technologies
1.1- Create a custom Error handling Attribute:
-Using HandleErrorAttribute or using IExceptionFilterFilter Showing example using HandleErrorAttribute.
1.2- Create a custom Error handling Attribute
-If you do not want to write attribute then you can set Custom Error page in Web.config file. Before doing that just create a simple Error page in HTML for displaying if any error occurs.

2- Cross-Site Request Forgery (CSRF):
- A CSRF vulnerability allows an attacker to force a validated and logged in user to perform actions without their consent or unknowingly.
- Microsoft has recognized this threat and for preventing the same we have something called as AntiForgeryToken.
** Solution:
We need to add @Html.AntiForgeryToken()helper in your form inside form tag .And on the Action Method which handles your post ([HttpPost])Request we need to put[ValidateAntiForgeryToken] attribute which will check if the token is valid.

-Working of AntiForgeryToken:
When we add AntiForgeryToken helper on View it creates a hidden field and assigns a unique token value to it and meanwhile a session Cookie is added to the browser.When we post formHTML it's checks for __RequestVerificationToken Hidden field and whether __RequestVerificationToken Cookie are present or not. If either the cookie or the form _RequestVerificationToken Hidden field values are missing, or the values don't match, ASP.NET MVC does not process the action. This is how we can prevent cross-site request forgery attack in asp.net MVC.
3- Cross-Site Scripting (XSS) Attacks:
- Cross-site Scripting (XSS) is an attack in which malicious scripts is injected via input fields this attack is most common and allows an attacker to steal credentials and valuable data that can lead to a big security breach.
- In short by default ASP.NET prevents Cross Site Script attack.But now what if we want to put SCRIPT tag.we have four ways via which we can allow scripts to be posted.
- solutions:
- [ValidateInput(false)].
- [AllowHtml].
- [RegularExpressionAttribute].
- AntiXSS Library.
3.1- [ValidateInput(false)]:
[ValidateInput] is an attribute which can be applied on Controller or Action Method on which we want the script to go through.

3.2- [AllowHtml]:
[AllowHtml] attributes that is applied to Model properties such that it will not validate that particular Model property on which AllowHtmlattribute is added.This allows submitting HTML for avoiding Cross Site Scripting attack.

3.3- [RegularExpression]:
The third solution to XSS attack is validating all your Fields with Regular Expression such that only valid data can move in.

3.4- [AntiXSS Library]:
We can use this Method to filter malicious script while saving in the database and displaying in the browser.
- install AntiXSSLibrary
- After installing we are going to have a look on how to use AntiXSSLibrary.
3.4.1- Sanitizer Class:
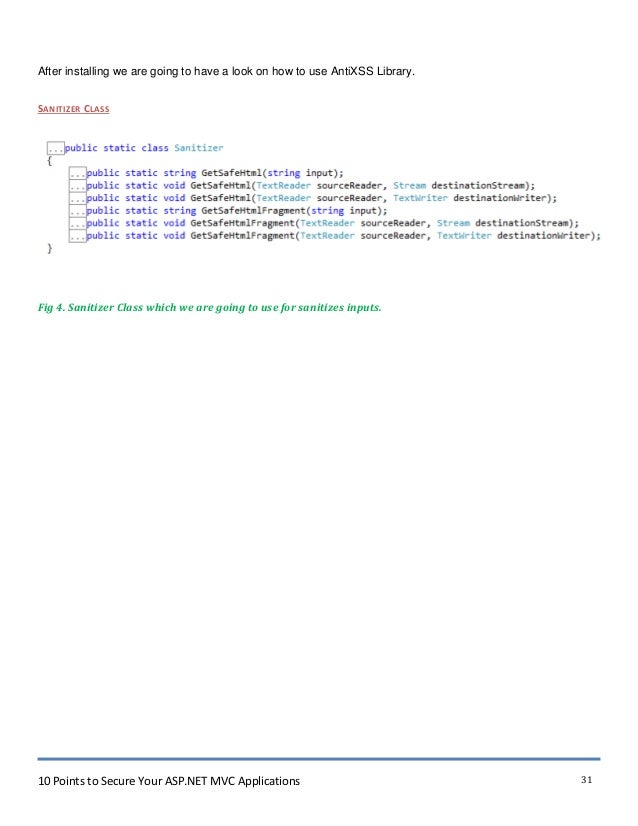
- Sanitizer class method (GetSafeHtmlFragment) will check and return your Sanitize string.

4- Malicious File Upload:
we need to protect from taking invalid input most attackers try to upload a malicious file which may cause a security issue. The attacker can change file extension [tuto.exe to tuto.jpeg] and the malicious script can be uploaded as an image file.
- Solution:-
- First thing we need to do is validate file uploads.
- Allow only access to files extension which are required.
- Check the file header.
5- Version Discloser:
- Version information can be used by anattacker to target specific attack on that Version which is disclosed .Whenever browser sends HTTP to request to the server in response we get response header which contains information of [Server, X-AspNet-Version,X-AspNetMvc-Version, X-Powered-By].
- The server shows information of which web server is begin used.
*X-AspNet-Versionshows information of which specific Asp.Net VersionUsed.
* X-AspNetMvc-Versionshows information of which ASP.NET MVC version Used.
* X-Powered-By shows information of which framework your website is running on.
Solution:-
- For removing X-AspNetMvc-Version header: Just set [MvcHandler.DisableMvcResponseHeader = true;] in Global.asax Application start event [Application_Start()] this will remove header it won’t be displayed any more.
- For removing X-AspNet-Version and Server header: Just add an event in [Application_PreSendRequestHeaders()] in global.asax and then to remove header we need to set the property as below.
- For removing X-Powered-Byheader: To remove response of X-Powered-Byheader which shows information of which framework your website is running on Just add this tag under System.webServer in Web.configfile will remove [X-Powered-By] header.
